Understanding LTE call flow in-depth
With Long Term Evolution (LTE) comes a myriad of new and exciting attributes. One of these is the LTE call flow itself. In fact, call flow and signaling is unique for LTE, and is driven by 3GPP standards. Call flow is how signaling and sessions are created across an LTE network.
So how does LTE call flow work exactly?
According to Wired n Wireless, the LTE call flow travels through many steps during its end-to-end signaling between from user equipment (UE) to the evolved node B (eNB), mobility management entity (MME), home subscribe server (HSS), serving gateway (SGW) and PDN gateway (PGW).
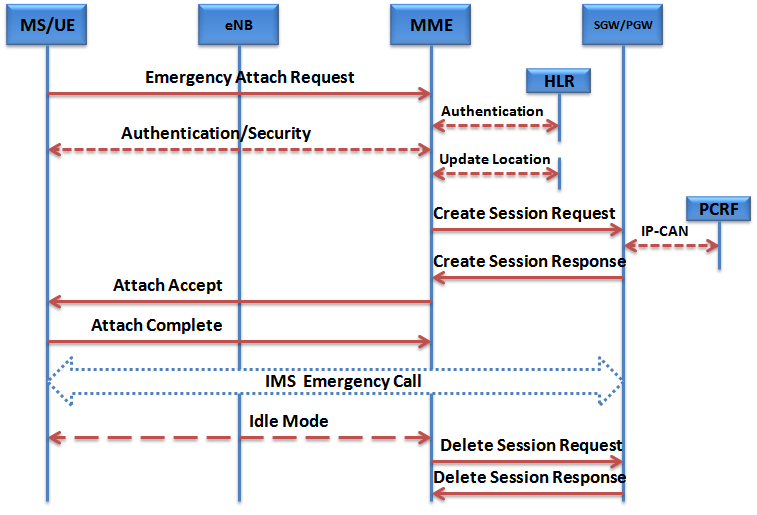
It begins with S1 Setup, where the eNB is initially attached to the network. The eNB supports the LTE air interface and includes the following functions:
- Functions for Radio Resource Management: Radio Bearer Control, Radio Admission Control, Connection
- Mobility Control, Dynamic allocation of resources to UEs in both uplink and downlink (scheduling)
- Selection of an MME at UE attachment when no routing to an MME can be determined from the information provided by the UE
- Routing of User Plane data towards Serving Gateway
- Scheduling and transmission of paging messages (originated from the MME)
- Scheduling and transmission of broadcast information (originated from the MME or O&M)
- Measurement and measurement reporting configuration for mobility and scheduling
As long the eNB is functioning properly, the S1 setup will stay intact. Once UE comes up a radio resource control (RRC) connection is established for communication with the network. After RRC is established, network attached storage (NAS) signaling begins.
UE then sends an attach request along with a PDN connectivity request to the network. Attach is for attaching to the network. Once MME receives the attach request, it queries the HSS for authentication details. HSS then sends the authentication vectors to MME in an authentication info answer. The next step in call flow for LTE has to do with authentication and security. The network requests UE for authentication vectors. When the UE provides the same one, MME compares it with what HSS has sent. If they match, the UE is authenticated. MME manages mobility, UE identities and security parameters. It includes the following functions:
- Non Access Stratum (NAS) signaling and security
- Idle mode UE reachability (including control and execution of paging retransmission)
- Tracking Area list management (for UE in idle and active mode)
- PDN GW and Serving GW selection;MME selection for handovers with MME change
- Roaming (terminating S6a towards home HSS)
- Authentication Bearer management functions including dedicated bearer establishment
Next security takes over and all NAS messages are encrypted using the security algorithms that were exchanged. After the LTE call flow moves through the security step, the network creates the EPS bearers. Then the radio bearers are created and RRC connections are modified accordingly. Once these radio bearers are created the eNB down link addresses are sent to SGW in GTP messages. The Serving Gateway is the node that terminates the interface towards EUTRAN. For each UE associated with the EPS, at a given point of time, there is one single Serving Gateway. Functions include:
- Packet routing and forwarding
- The local mobility anchor point for inter eNB handover
- E-UTRAN idle mode downlink packet buffering and initiation of network triggered service request procedure
- E-UTRAN idle mode downlink packet buffering and initiation of network triggered service request procedure
- Accounting on user and QoS Class Identifier (QCI) granularity for inter-operator charging
- UL and DL charging per UE, PDN, and QCI
- End marker handling
- Packet Filtering with TFT
It seems technical, but LTE call flow is a technical process!
To further understand this process, please see the LTE call flow diagram, also created by Wired n Wireless.

