Evolving network opportunities available through advances in software require an adjustment in how we view the network
It’s interesting how casually we accept exponential-growth concepts like mobile, social and ultimately the “internet of things.” The impending differentials in size of the device universe – from billions to trillions – doesn’t faze us at first; that is until we begin to think about how network designs could possibly support such a creative explosion. Despite 20 years of internet protocol experience, the answers just won’t come.
Our limitation is not technology, it’s us. Humans are prone to something cognitive psychologists call “anchoring,” in which our answers to new thought challenges cling to old frames of reference. We don’t swing far enough away from that anchor to discover where the real answers lie.
To unleash the design creativity necessary for new IP networks that can support the exponential growth of devices and traffic, we have to reach deep into our architectural souls to find the fundamental assumptions to which we are clinging. We need to shine a light on them and challenge those aggressively. It’s time to rethink.
Rethinking the network edge
It doesn’t matter how far-flung a network design may be, when we visualize it there is always a firm end we know as the network edge. Connectivity begins and ends with access. For corporate uses, customer premise equipment embodies that finite edge. We know that the software within CPE performs the required network services, playing pitcher/catcher with upstream provider equipment. However, within this traditional worldview hides multiple assumptions.
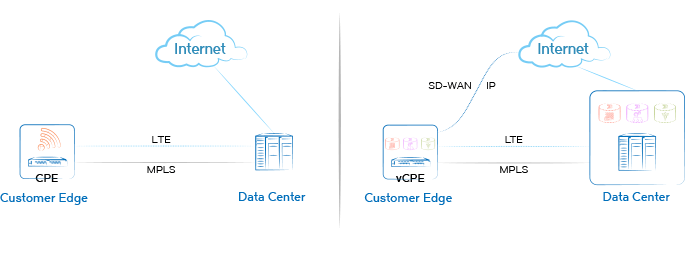
Fixed physical location
The cloud taught us that we don’t have to be next to a device to derive its benefits. A wide range of network services can actually be performed remotely from a provider’s data center. A simple tunnel from the premise to the cloud is all that is needed; routing, firewalling, virtual private network termination and other services can be remote. Where did the network edge go?
Function-specific devices
We know virtual data centers or clouds are shared-hardware environments, but we assume CPE is single-function and physically managed. New virtual CPE system architectures are changing that. Network services can stack up within a modern hardware design and new services can be launched with a remotely delivered software load. Physical constraints of logistics and inventory become a thing of the past.
Singular network attachment
We know CPE is an endpoint to a provider’s network, a single point of ingress/egress to a Multiprotocol Label Switching walled garden. This network edge is effectively the end of the road, but a new split personality is coming to CPE, trading off traffic between the expensive proprietary network and a cost-effective internet link. With this SD-WAN behavior, the network edge is no longer an end point; it’s become a jumping-off point to another universe.
The new network edge is becoming an ephemeral concept. It is moving, morphing and multimoding.
Rethinking aggregation
Traffic aggregation is a mainstay of IP network designs. It’s a massive unstated assumption; we visualize aggregation points in the network and never challenge the concept. Aggregation is a “scale up” technique that can be a key impediment to effectively “scaling out” a network design. Making changes or addressing maintenance requires long planning cycles, not to mention the difficulty in cost-effectively forecasting and delivering capacity requirements for growth.
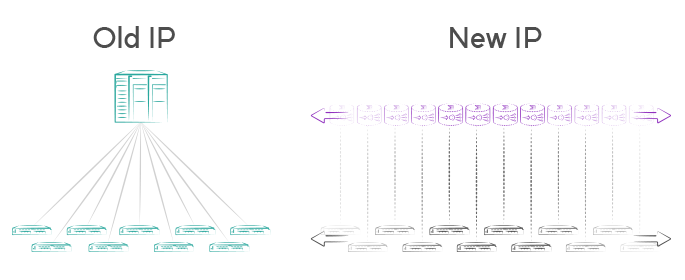
Network functions virtualization changes this worldview dramatically. We can realize better network designs with one-to-one relationships instead of communal ones. Terminating VPNs in lightweight virtual routers, or giving every application its own virtual analog-to-digital converter are examples of how service scale out can be effectively delivered in a way that puts an end to the limitations of aggregation.
Rethinking security
There have always been active adversaries intentionally trying to break into systems. In the past it was hard for the bad guys to get enough information to succeed since each component in the system was proprietary, vendor-specific and had little to no commonality with its surrounding components. Today’s adversaries are far more active, primarily because information about how components are designed and work is more widely available. This information is accelerating the tools at their disposal and is rapidly expanding the universe of knowledge about attack surfaces and vectors. It has become asymmetric warfare.
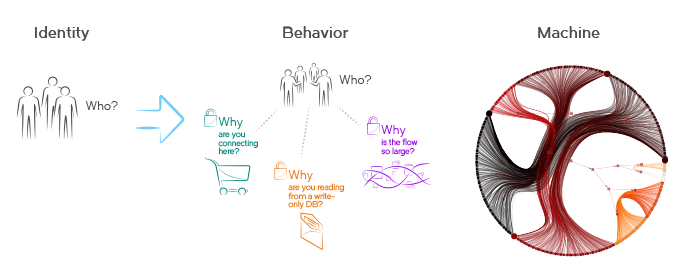
Vendors and network operators must move beyond static approaches to security design. Dynamic models that focus on network behavior rather than user identity are required for remediation, observation and estimation. Machine learning, software-defined networking control and automation are rapidly becoming the new normal against more sophisticated adversaries.
Rethinking control
When SDN burst onto the public stage in 2011, it began with a very limited dialogue around basic level-two switching. Much of that perception has held, despite the fact the broader challenge is programmatic control over every type of network element, whether physical or virtual, including those sourced from a heterogeneous mix of vendors.
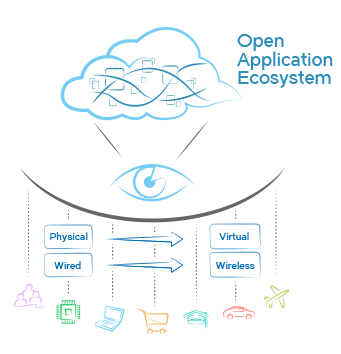
To achieve new designs we must change this worldview. Control must assume it applies to the whole network. From that assumption managers must turn their focus to specific applications that run on the control layer. There will not be a single SDN killer app; a wide range of apps will come into existence. Controllers without applications are as limited in use as controllers with limited southbound options.
Rethinking automation
Far too large a percentage of network budgets are utilized simply for maintenance. As the network transforms through overlays, NFV-based services and SDN control, we need to stop thinking about automating our interface to devices and focus on automating networking. To get there, we must shift our thinking to “workflows.”
Workflows start and end outside the network, triggered by applications, subscribers, tenants, etc. Because they cross resource boundaries and teams, the majority of a workflow’s elapsed time occurs in passing tickets, scheduling change reviews, standardizing activities and so on. Automating these handoffs removes the inherent delays as requests are volleyed between teams. Focusing on workflows is where the real benefits of automation will pay off. The leverage from automation will allow reallocation of resources from maintenance to innovation capacity.
In total, the challenges facing networking are massive and nonlinear. Success will be found in agile, open and dynamic designs that are free of long-held, outdated conceptual anchors.
Kelly Herrell is SVP and GM of software networking at Brocade. He leads software networking strategy and execution at the company. Herrell previously served as CEO of Vyatta, a pioneer and industry leader of virtual routing, which was acquired by Brocade in 2012.
Editor’s Note: In an attempt to broaden our interaction with our readers we have created this Reader Forum for those with something meaningful to say to the wireless industry. We want to keep this as open as possible, but we maintain some editorial control to keep it free of commercials or attacks. Please send along submissions for this section to our editors at: dmeyer@rcrwireless.com.

