The Motorola Atrix 4G was the first smartphone with a fingerprint scanner for quicker, more secure log in authentication. But the security feature’s widespread use came about when Apple introduced it in its iPhone 5s back in 2013. Since then, Snapdragon-powered Android phones have made it a stock feature in premium models, trickling down to mid-range and even budget devices for a new level of smartphone security. That new feature alone has the important function of keeping our ever-increasingly important devices safe from breaches.
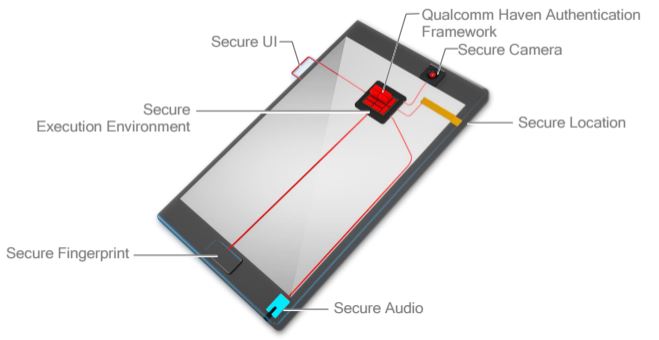
But even a fingerprint sensor is not 100% reliable, or secure. In a session on security and machine learning at the Qualcomm 4G/5G Summit, Sy Choudhury, senior director of product management at Qualcomm, spoke of alternative and complementary methods for fortifying security for connected devices. Choudhury likened security to hygiene, questioning where a company should start, and where to end, when putting resources into security.
He said the only way to make sure a device is secure is by doing three things:
- Ensure that hardware is securely integrated into the device.
- The authenticator code has to run in a secure execution environment.
- Data has to be stored in a secure file system.
It is also important to make sure OEMs work with their vendors as Choudhury claims half the devices currently released are not doing all three steps.
One way Qualcomm is looking to enhance its security efforts is by encrypting on a file-by-file basis (file-level encryption or Direct Boot), instead of looking at the full disk, a necessary requirement for Android O (the OS update after 7.0 Nougat), according to Choudhury. This allows different files to be encrypted with different keys that can be unlocked independently. Google previously required mandatory full-disk encryption for devices running its 6.0 Marshmallow operating system.
Choudhury said security companies are working to trial new features and push regulations. Enterprises are another segment looking for better device security by using data from the devices to know about the state of the handset (Attestation).
Both security companies and enterprises are coming to Qualcomm to find out the state of users, answering important questions like, Is user the correct user? What is the state of device? Has there been malware on this device and when? Where is it located?
Of course, it is important that smartphones authenticate only the appropriate users wanting to access devices and the private data they house. According to Choudhury, the fingerprint sensor is a use case for securing a device, it is not an outright solution. OEMs are looking for ways to further secure devices beyond the fingerprint sensor using both software and hardware. He gave a number of up-and-coming use cases for smartphone security by making Authentication and Attestation richer:
Iris
- The iris, a structure within your eye, has more entropy (randomness) in data than fingerprints, according to Choudhury. He claims many tech providers already have iris-based authentication, and its compact size allows for continuous security within the execution environment. One disadvantage is that iris scanning requires a second IR camera, which currently costs between three and four dollars of materials. It also has some nuances, like inaccuracy when wearing glasses. The now recalled Samsung Galaxy Note was the first commercial smartphone to use iris scanning for security.
Retina
- Retina authentication uses the shape of the eye and its veins. According to Choudhury, only a few tech provider are working on reliable, consume level retina authentication. There is currently no bill of materials for retina as you can use a standard RGB camera. One disadvantage is that it requires high levels of computation using algorithms, making it push both the device’s CPU and GPU.
Face detection
- Your face isn’t unique enough to be used by itself like your fingerprint. However, using the sides of your face can do much more unique authentication. One downside is that most payment companies will not accept face, as they look for something with more entropy.
Choudhury said that your eye won’t singularly replace fingerprint authentication, in fact, the goal is to use multi-factor, or strong authentication, to increase accuracy, especially for high transaction payments.

