5G security is fundamentally better than LTE security but the attack surface is massively increased
In the ongoing generational shift from LTE to 5G, network security is top of mind for carriers and governments, particularly as it relates to Chinese ICT giant Huawei Technologies. While Huawei has had difficulties in the U.S. and markets where the U.S. wields political influence, it remains the leader among its comp set of vendors.
Domestically, federal lawmakers could allocate $2 billion to fund the rip-and-replace of Huawei equipment already deployed in rural and regional U.S. networks.
In recent comments, Huawei’s CTO for the Carrier Business Group, Paul Scanlan, discussed some of the broad issues surrounding 5G security and the collaborative nature of developing relevant industry standards.
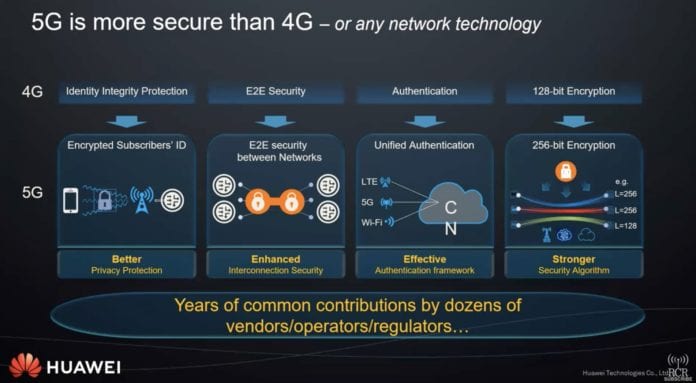
In the upgrade from LTE to 5G, Scanlan noted that, “The first ting was that we increased the encryption from 128- to 256-bits. More importantly, what we did was we provided all the information in pretty much like a [Secure Sockets Layer] or tunnel. It goes all the way through the base station, over the transport network, back into the core. It doesn’t matter whether it’s a Huawei radio or base station, or an Ericsson or Nokia or anybody else’s. The point is the manufacturer of those can’t see any data.”
On the standardizations point, Scanlan pointed out that 5G is. result of decades of technical specification work done through industry organizations like the 3GPP and ETSI. “Their members are from pretty much every vendor…every government, regulator, as well as telecom operators around the world. It doesn’t matter which continent you’re in or which political party you belong to–they’re all there.”
Scanlan also discussed the move with 5G to virtualized networks running in hybrid- or multi-cloud-type environments. This is what will ultimately support end-to-end network slicing wherein multiple virtual networks capable of supporting applications with varying service requirements are operated on a single network infrastructure. This complexity is further compounded when you add in the need to distribute computing power closer to the edge of the network to leverage the latency reductions of 5G through running workloads closer to where the applicable data is generated.
With MEC, Scanlan said you introduce new “physical security” exposure in addition to the existing cyber security attack surface.
“There’s a lot more components in a network than worrying about, quite frankly…a vendor or whether or not you think he is secure.”