While Wi-Fi 6 and 5G may both be secure, important questions about data ownership remain
Historically, one of Wi-Fi’s biggest drawbacks, particularly in comparison to cellular, was the level of security it could offer. Unlike Wi-Fi, wireless cellular technology has the wireless security layer as well as the security offered by authentication for the SIM card, which was introduced in 2G. Adam Smith, LitePoint’s director of product marketing, indicated that these features make 5G more secure option for a business or venue.
However, Wi-Fi Alliance’s Senior Vice President of Marketing Kevin Robinson pushed back on this premise slightly, pointing out that it’s important to compare like deployment models.
“If you want to compare the security that W-Fi offers when you have to a device that has been provisioned with a credential and compare that to cellular security, you will find that both Wi-Fi and cellular deliver adequate security for that model,” he said. “They both meet the requirements.”
Wi-Fi, he added, offers an incredibly flexible deployment architecture that can go from an unauthenticated network all the way up to a very secure enterprise or government network.
Beyond this fact, the Wi-Fi Alliance launched the next level of Wi-Fi security, WPA3 and Wi-Fi Enhanced Open, which as of July 1, 2020, must be included in every W-Fi certified device. WPA3 is expected to be able to handle the flexibility Robinson referred to, spanning use cases ranging from those with no security needs at all to those requiring government-class security.
Smith agreed that with the recent WPA3 update, Wi-Fi 6 and 5G are much more comparable from a security perspective, and that Wi-Fi is now “basically on par with any cellular security at the physical layer.”
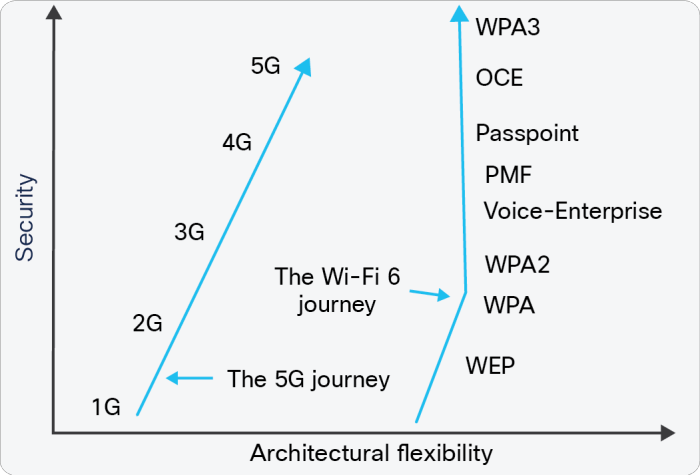
At the same time that Wi-Fi is trying to improve its security to be a more reliable choice for handling data of different kinds, cellular is trying to become more than just a mobile technology, which means enabling more flexibility.
Robinson provided further detail: “Cellular is moving more towards things Wi-Fi has already been doing, like with extensible authentication protocol (EAP), so [cellular is] actually leveraging many of the technologies that Wi-Fi was already using.”
“The reason for this, and why Wi-Fi sometimes gets picked on,” Robinson continued, “is that Wi-Fi doesn’t just support a single deployment model. Wi-Fi supports a wide range of deployment models to include an unauthenticated experience where you walk into a coffee shop, don’t tell anyone who you are and join a network. Try doing that with your cell phone.”
The problem with an increase in cellular network flexibility, though, said Smith, is that as you add flexibility, you create concerns around who has access to the data.
Data ownership
Extreme Networks’ Director of Product Marketing Perry Correll also thinks that companies should be thinking critically about data ownership in a 5G era.
While reading an article about Verizon’s plan to have 5G signals carried from inside a business or a home to the carrier’s small cell base station outside where the carriers will then send the traffic to the carrier’s core network, he hesitated.
“When I read that,” he explained, “the first thing that resonated with me was the part about all that data going back to the carrier. As an enterprise, as a business, how am I going to get that data back to me?”
Data procurement and analysis has become immensely critical in business operations because with that data, you can apply machine learning and artificial intelligence, which have the potential to drastically improve various aspects of a business.
“If we get into an environment where we’ve replaced all of the Wi-Fi devices with some type of small cell base station and we’ve shifted away from Wi-Fi to a carrier-based network, then all that data for what’s happening on my network is actually going to the carrier’s network,” Correll reasoned.
And from there, what happens to that data?
“Do I, as an enterprise or business, have free access to that data? Can I go in and hit a cloud service and see everything and pull it back down to me? Do I need to license it?” he asked, admitting that he just doesn’t know yet.
“I can only assume that there is going to be a variety of answers to those questions based on where you are in the world with different rules and that different vendors might have different packages available to you,” he said.
Either way, Correll believes that there needs to be a process in place that doesn’t exist today to address data ownership when that data is on a cellular network.
In his opinion, conversation around this particular topic is lacking because when people think about cellular communication, they think about smartphones. However, in a pure 5G environment, or even a Wi-Fi and 5G venue environment, other devices like laptops, tablets, IoT devices and any other wireless-enabled devices will be on the network.
“Right now, if I have a Wi-Fi access point sitting there and I have data flowing through it, it’s mine […] and I can do what I want with it as far as tracking of whatever applications are running on my network,” he said. “But in a pure 5G environment, all that data that’s flowing through them is going to somebody else first.”

