Network slicing is not widely deployed; AdaptiveMobile Security working with GSMA on a fix
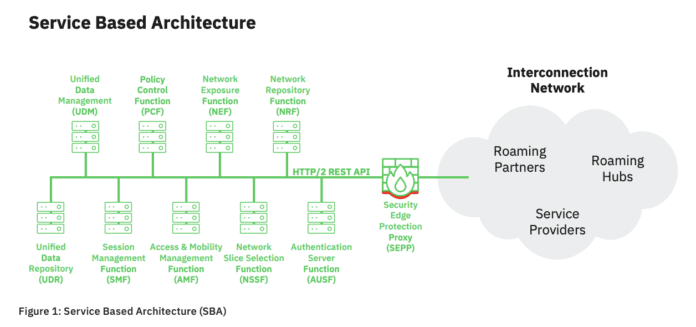
Network slicing is among the North Stars of current 5G efforts as the ability to virtually partition a network out from the core to the radio access network is seen as instrumental in providing differentiated, monetizable enterprise services. While network slicing is today not in common use anywhere in the world, specialist firm AdaptiveMobile Security has released research calling out a “major security flaw” associated with the architecture of network slicing.
In the paper, AdaptiveMobile Security said the relevant standards in place to day may not be sufficient to protect virtualized slices from “user data extraction – in particular location tracking; denial of service against network function; [and] access to a network function and related information of another vertical.”
AdaptiveMobile Security has detailed its finding in a Common Vulnerability Disclosure to industry body GSMA.
AdaptiveMobile Security’s Head of 5G Security Research Silke Holtmanns said that bringing IT technologies to telecoms can “increase efficiency and improve functionality. However, while laudable, there needs to be a wider mindset change. When it comes to securing 5G, the telecoms industry needs to embrace a holistic and collaborative approach to secure networks across standards bodies, working groups, operators and vendors.”
Click here to download the full paper, “A Slice in Time: Slicing Security in 5G Core Networks.”
GMSA Head of Security James Moran told Light Reading that “the attacks described in the research paper have not been demonstrated in any live environments…A number of measures that can be effectively mitigate the reported threats have been identified and GSMA will be submitting its recommendations to 3GPP in the coming days to ensure the necessary standardization work can be done well ahead of the rollout of 5G core network slicing.”