Comcast Business says it mitigated 24,845 multi-vector DDoS attacks in 2021
Distributed denial-of-service (DDoS) DDoS attacks refer to a malicious actor or actors temporarily or indefinitely disrupting services of a host connected to a network to render an entire network or website unavailable. While larger-scale DDoS attacks are predicted to rise, a new breed of shorter, faster threats called multi-vector attacks are emerging.
As the name implies, during a multi-vector DDoS attack, bad actors infiltrate a network using multiple entry points or “vectors.” Common vectors include emails, databases and web browsers. The goal can be to take down a target’s network or to obtain sensitive data.
“For example, a hacker could simultaneously carry out both a volumetric and network protocol attack against a target. In this way, if one attack fails, the other attack may be able to succeed,” A10 Networks explained in a blog post. In 2018, the company found that multi-vector attacks accounted for 75% of the 3,000 DDoS attacks that occur daily at the time.
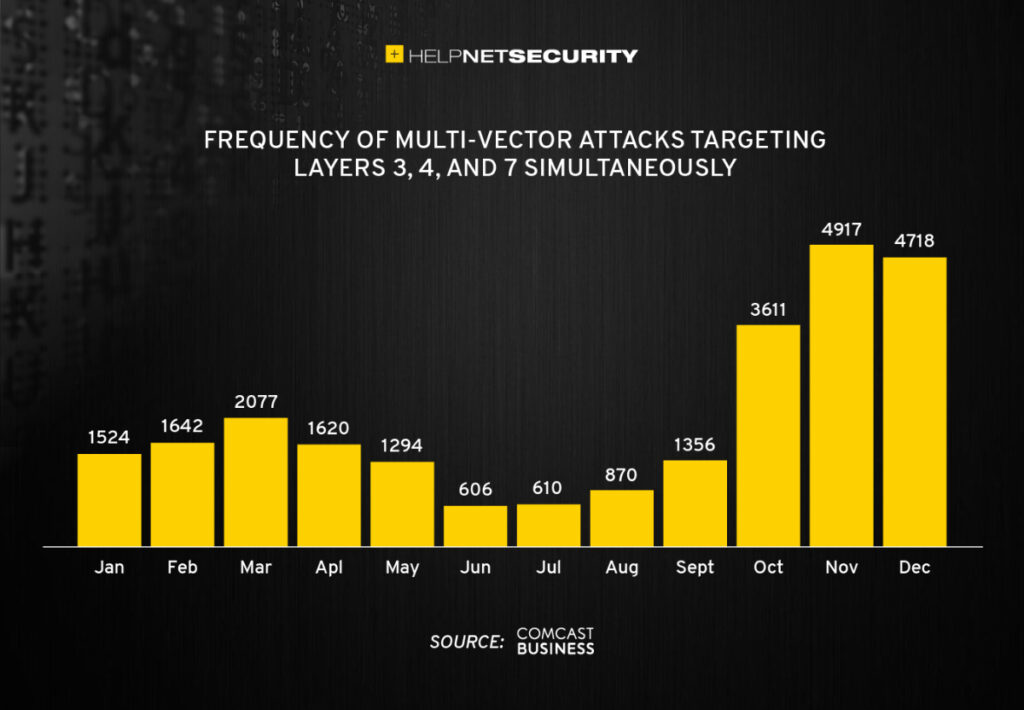
Since their emergence only a few years ago, multi-vector attacks have become increasingly common. In a 2022 report, Comcast Business revealed that it mitigated 24,845 multi-vector DDoS attacks in 2021, a 47% increase over 2020. Sixty-nine percent of Comcast’s customers experienced DDoS attacks in 2021, and 55% of those were targets of multi-vector attacks. In 2020, claimed Comcast, most customers experienced single vector attacks, pointing again to a changing cybersecurity landscape.
The majority of multi-vector attacks in 2021, Comcast found, were under 5 Gbps and lasted under 10 minutes. That’s because lower volumes and shorter durations are harder to detect. Also notable is the fact that the number of vectors used in such attacks increased year-over-year from five to 15.
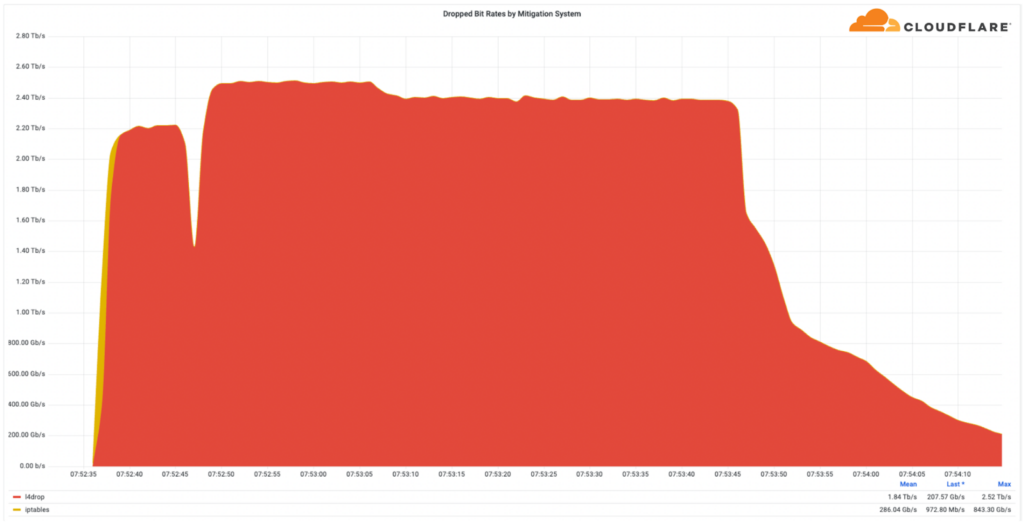
In Q3 2022, IT services management company Cloudflare mitigated a 2.5 Tbps multi-vector DDoS attack launched by a Mirai botnet variant, aimed at the Minecraft server, Wynncraft. The company said that from a bitrate perspective, it was the largest attack it had ever seen. Fortunately for the hundreds and thousands of gamers playing on the Wynncraft server, Cloudflare was able to automatically detect and filter out the attack. The company claims that users didn’t even notice.
According to Netscout’s Threat Intelligence Lead Richard Hummel, these “shorter, faster, harder-hitting complex multi-vector attacks” will continue. “Adversaries increased attacks against online platforms and services crucial in an increasingly digital world, such as e-commerce, education, financial services, and healthcare,” said Hummel. “No matter the target, adversary, or tactic used, it remains imperative that defenders and security professionals remain vigilant in these challenging days to protect the critical infrastructure that connects and enables the modern world.”

