The DNS layer is considered the ‘phonebook’ of the internet
During an application or Layer 7 distributed denial-of-service (DDoS) attack, a bad actor or actors exploit weaknesses in the layer of a website that interfaces between human input and the site’s technical backend. In Layer 7, there are two protocols that are typically the focus of such attacks: Hypertext Transfer Protocol HTTP and Domain Name System (DNS).
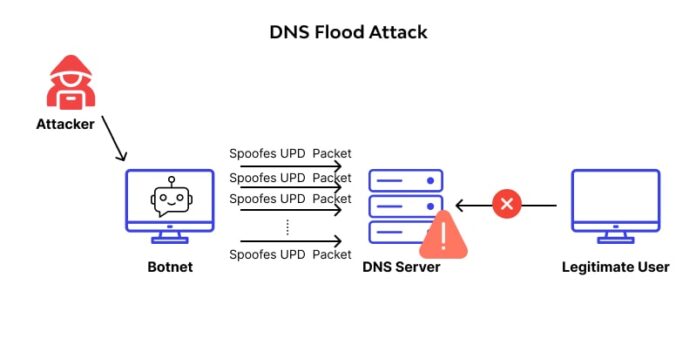
In a DNS flood, an attacker can initiate a flood of seemingly legitimate DNS requests. According to Cisco, DNS can be considered the “foundation” of the internet. That’s because this layer acts as a sort of “phonebook” by translating human-language client application requests — such as rcrwireless.com — into IP addresses, allowing the user to navigate to the desired website.
In a DNS flood, a bad actor[s] targets one or more DNS servers to disrupt DNS resolution for that domain. “If a user is unable to find the phonebook, it cannot lookup the address in order to make the call for a particular resource,” explained DDoS mitigation provider Cloudflare. “By disrupting DNS resolution, a DNS flood attack will compromise a website, API, or web application’s ability to respond to legitimate traffic.”
Cloudflare added that such attacks are tricky to spot because the large volume of traffic often comes from a variety of unique locations, requesting real, existing records on the domain, and therefore, mimicking legitimate traffic.
How to defend against DNS flood attacks
Data centers and enterprises can protect against DNS flood attacks by logging and monitoring all DNS requests, locking the DNS cache, as well as having sufficient DNS-layer security protocols that can alert to any odd or suspicious DNS activity. Using a DDoS mitigation service from a trusted partner can also go a long way in protecting against these types of attacks because these vendors can provide recursive DNS servers, which lookup where one DNS server communicates with several other DNS servers. This differs from iterative DNS queries, where the client communicates directly with each DNS server involved. Recursive DNS servers can identify and thwart harmful DNS connections before they cause too much damage.