DDoS attacks targeting commercial data centers are becoming more frequent, bigger and smarter
Distributed denial-of-service (DDoS) attacks refer to a malicious actor or actors temporarily or indefinitely disrupting services of a host connected to a network to render an entire network or website unavailable. While there are various types of DDoS attacks — such as multi-vector attacks and volumetric attacks, just to name a few — it’s most important to understand that such attacks occur when multiple systems target a single system with a DoS attack and typically target edge network devices like routers and switches, rather than individual servers, and the impact of such an attack can include things like loss of productivity and critical services or communications, extensive costs associated with remediation and downtime, as well as damage to brand reputation.
DDos attacks: ‘more intense, more frequent’
Over the last few years, the threat posed by such attacks has increased at an alarming pace. In fact, in its Q1 2022 DDoS Threat Report, A10 Networks found that DDoS weapons nearly tripled over the past two years. Worse still, the frequency, magnitude and sophistication of DDoS attacks has grown as botnets and automated attack tools are readily available to cyber criminals. Another development is the growing awareness of such attacks as numerous high-profile incidents have shined a light on the potential extent and impact of such breaches.
Last summer, for example, Google was hit with the largest application layer DDoS ever recorded. The attack peaked at 46 million requests per second and was at least 76% larger than the previously reported record, which was mitigated by IT management company Cloudflare. Google’s network security service Cloud Armor was able to detect and block the massive attack, and the targeted customer’s service stayed online.
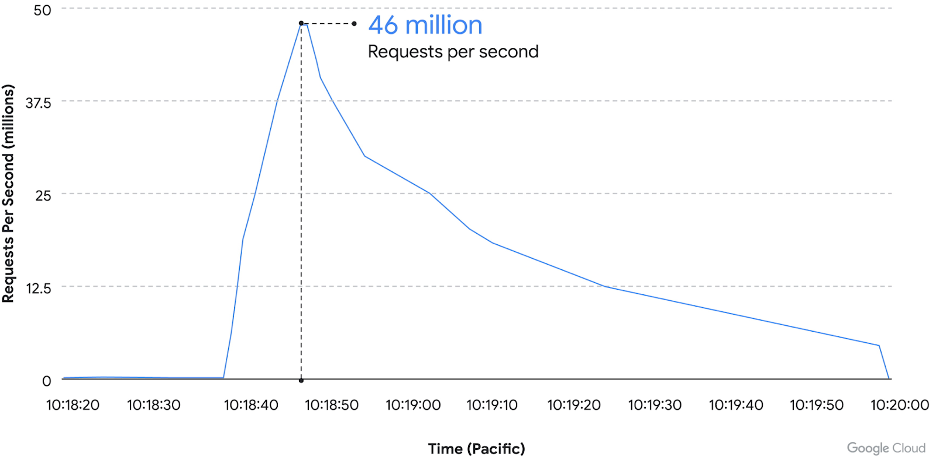
“To give a sense of the scale of the attack, that is like receiving all the daily requests to Wikipedia (one of the top 10 trafficked websites in the world) in just 10 seconds,” Senior Product Manager of Cloud Armor Emil Kiner and Technical Lead at Google Satya Konduru wrote in a blog post. “Attack sizes will continue to grow and tactics will continue to evolve,” they added.

“Every year it gets more intense and more frequent [and] there’s a much greater awareness of cyber threats in the public and in enterprises,” A10 Network’s Director of Service Provider Product Marketing Terry Young told RCR Wireless News, adding that the COVID-19 pandemic likely kicked these attacks, and therefore, the awareness of them, “up a notch.”
Young explained that not only are DDoS attacks that target commercial data centers becoming more frequent, they are also getting bigger and smarter. “The data center industry is just booming — it’s being built everywhere, and that’s the result of people creating more and more traffic and enterprises putting more workloads into either their own data centers or public data centers,” she said.
She added that data center operators that lease out to customers don’t often have cybersecurity protocols built into their business models because that requires them to provide a more complex type of customer support. “But I think partly because of the public awareness of the impact of DDoS attacks or any other kind of cyber threat… there’s a level of scrutiny that I think was not there a few years ago, and I think it kind of sets a tone for data center projects… and that more is going to be expected of them,” she stated.
As a result, Young continued, data center providers are looking to expand their cybersecurity portfolio to include managed services like DDoS protection-as-a-service, or to simply improve the measures already in place. “Even small SPs [service providers], as they’re building out, are trying to future-proof their network; they’re starting to consider these threats, and looking at what kind of DDoS defenses can they put in place,” she argued.
How can data centers protect themselves from DDoS attacks?
Damian Menscher, one of the lead engineers on Google’s DoS Security SRE team, urged organizations to have “multiple layers of defenses.” It’s important, he said, to be able to assess if the traffic getting into your network is “good or bad.” Google is fortunate to have a massive amount of capacity, which allows it to take in a lot of traffic and then use its multiple layers of defenses to assess the traffic’s legitimacy as it enters its network. “Once it’s on our network, we have multiple layers of defenses where we can look at the traffic just as it’s entering our network and then it’s entering an individual data center, and then — if it’s an application layer attack, for example — we can look at every individual request that is being sent and evaluate if it’s valid,” he provided, adding that Google has started to make some of these defense capabilities available to its customers.

But not everyone is Google and not every company needs the same rigorous protections, simply because they’re smaller targets. Therefore, when it comes to protecting your network from DDoS attacks, Menscher said it’s not really a one-size-fits-all situation: “Different places may be focused on different threats depending on where they fit in their business or what their business concerns are,” he offered. “It’s important for them to think about how much they are actually going to spend on mitigation. In many cases, they may enable a sort of fallback mechanism. So if they are attacked, they can find a cloud DoS mitigation provider to step in and help them at that time.” He added that some entities, like a small internet service provider, their upstream provider may already provide some DDoS defense capabilities, so they should speak with these providers to see what options are available.
However, Young pointed out that this doesn’t mean smaller organizations and data centers shouldn’t take serious precautions to prevent and mitigate the effects of DDoS attacks. “The only time you read about [DDoS attacks] is when there’s huge attacks. Microsoft had one last year; it was a 3.4 terabit size attack that they mitigated. So everyone hears about that and the smaller ISPs go, ‘yeah, no one’s going to attack me with that.’ Well, the truth is, most attacks are really small,” she warned, adding that most attacks are under 10 gigs, and these can absolutely impact smaller organizations.
Regardless of how an organization chooses to tackle the growing intensity and number of DDoS attacks, Young issued the reminder that cybersecurity should be considered a key capability that can set a company apart when it comes to customer experience and trust, as well as the ability to “grow in a cost-effective manner.”
At the end of the day, though, Menscher advises companies not to panic, even as instances of DDoS attacks in general are increasing both in frequency and size: “Exponential growth is expected in computers — we expect computers to increase in power over time, hard drives get larger, networks get faster — so if attacks get larger, that is totally normal and expected. I don’t tend to panic over these things. I think it’s helpful to know what to plan for but certainly I don’t think the world is coming to an end over any of this,” he shared.

