As enterprises embrace private wireless technology to improve the reliability demanded by new Industry 4.0 use cases, cyber security remains a predominant concern among both technical and non-technical leaders. That concern continues to intensify as organizations are hammered with the challenges of ransomware, insecure IoT devices, and insufficient resources to secure it all.
Private wireless networks, or so called 5G LANs, leverage the same cellular technology that powers our smartphones and other mobile devices to create a dedicated, secure wireless network that is isolated from the Internet.
Support for Zero Trust Networking
5G LANs support zero trust strategies with strong device identification, mutual authentication, granular end-to-end segmentation, and robust encryption – plus integrations via APIs and secure authentication standards such as Security Assertion Markup Language (SAML) for privileged access management.
New 5G LAN architectures tightly integrate with existing enterprise policies, user data plane constructs and security infrastructure tools (e.g., firewalls) already in place to create a unified risk management approach that reduces gaps in visibility to support even the most stringent regulatory requirements.
Private wireless networks prohibit risky uncoordinated peer communications and overlay protocols designed to subvert enterprise networks, such as multicast DNS and zero configuration networking technologies commonly found in enterprise Wi-Fi networks.
Strong device identification and authentication
One key challenge for securing the volume of disparate endpoints on any enterprise network is proper identification and classification of the device — two tasks that must be completed before security controls can be enforced.
Modern private wireless systems combine the deterministic and immutable identities inherent in cellular technologies with translated identities for integration with the enterprise LAN security controls such as VLANs and network access controls.
One of the primary reasons why private cellular networks are more secure than conventional enterprise Wi-Fi is the way they handle authentication.
With Wi-Fi networks, devices connect using a pre-shared key (PSK) or a network password that is manually entered. While convenient for users, it is also a major security vulnerability. Cybercriminals can easily gain access to the network by stealing the PSK or password or by exploiting weaknesses in the WPA2 protocol, which is commonly used to encrypt Wi-Fi traffic.
In contrast, private cellular networks use SIM cards or electronic SIMs (eSIMs) to authenticate devices. SIM cards help provide more secure identification so only authorized devices with valid SIM cards can connect to the network. This eliminates the risk of unauthorized access and ensures that all traffic on the network is encrypted and secure. IMEI and IMSI (International Mobile sub subscriber Identity) identifiers can be bound together to ensure SIM credentials can’t be used in different, unauthorized, devices.
What’s more, a new approach to concealing the user identity, called SUCI (the Subscription Concealed Identifier) is now being used to encrypt the user’s IMSI (now referred to as SUPI) on the SIM card before it leaves the device.
Within a 5G LAN, connected devices join the network using strong mutual authentication. This process authenticates both the endpoint to the network and the network to the endpoint to effectively mitigate man-in-the-middle attacks and spoofed or rogue devices. In addition, the infrastructure components arrive already hardened and use certificate-based authentication.
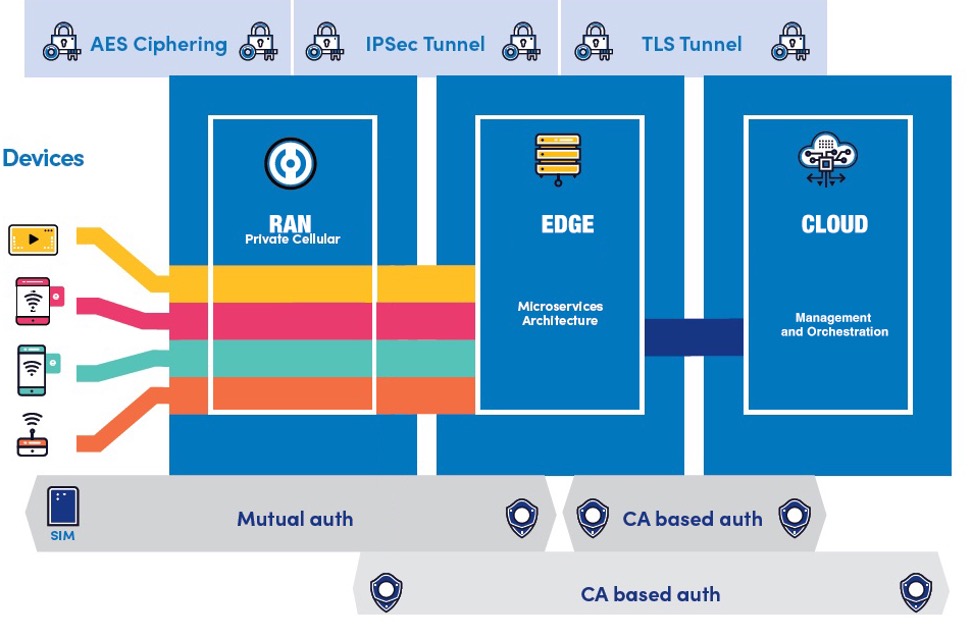
Device authentication protocols include 5G-AKA and EAP-AKA which bring enhanced flexibility and security to the authentication process by adding signaling and data integrity and confidentiality.
Granular end-to-end traffic segmentation
Another key element of a zero-trust architecture is segmentation. Recent technical advances in 5G LAN technology expands on the conventional 5G network slicing concept to deliver more granular control and security for devices or applications.
This allows enterprises to not only segment but separately encrypt individual devices or applications on a per-IP flow basis. When 5G LAN data traverses the enterprise LAN, AAA policies can be applied from the existing enterprise RADIUS services. The policies are configured just as they are for Wi-Fi and provide centrally managed authorization for dynamic VLANs or ACLs and support for change of authorization.
Robust data encryption
Data confidentiality and integrity are paramount, especially over wireless communication mediums. While prior generations of cellular technology relied on cryptographically weak algorithms and key lengths, 5G technology offers secure 128-bit AES encryption over-the-air, on par with the latest Wi-Fi WPA3 security standards. 5G LANs further extend protection with AES encryption, offering a cryptographic strength approved for use in the world’s most secure environments.
Advanced private wireless solutions offer enhancements for key derivation and rotation where the master key is never shared or exposed, and the device’s identity is concealed for enhanced privacy.
Complete control and privacy
Unlike public cellular services, Private wireless networks give enterprises complete data path control for privacy and compliance. All enterprise data remains local and under the control of the organization — alleviating privacy concerns of public 5G services or virtual private network slices offered by mobile network operators.
Corporate data is never visible, and all endpoint payloads are secured and contained within the enterprise 5G LAN. Only metadata and system performance metrics are typically sent outside the enterprise LAN over a secure TLS tunnel to a cloud-hosted orchestration system for administration and management.
By leveraging the same cellular infrastructure that powers our smartphones and other mobile devices, private cellular networks provide end-to-end encryption, secure authentication, and isolation from the public internet. They also offer better control and visibility over network traffic and are highly scalable, making them an ideal solution for enterprise environments.
As the number of network-connected devices continues to increase, it is likely that more organizations adopt private cellular networks to better secure their wireless networks and protect against cyberattacks.

