As organizations rush to automate factories, warehouses, and other industrial environments, deterministic network connectivity and uninterrupted mobility have become nonnegotiable. An increasing number of network-connected devices are being introduced into industrial operations at a faster pace than ever before while wireless connectivity has opened new doors for many mobile applications within the industrial sector.
While great news for advancing digital transformation efforts, one little discussed but big issue facing both IT and OT staff is how best to convert wired systems that reliably transport time sensitive protocols, used by elaborate process automation systems, over to a wireless network. Many of the essential systems used to achieve the holy grail of process automation, such as automated guided vehicles (AGVs), manufacturing robots and various process production equipment, simply don’t work well over wireless networks.
And the reason why can often be described in a single word: PROFINET. Moreover, the inability for wireless networks to support legacy process automation protocols like PROFINET is hampering digital transformation efforts.
THE PROBLEM WITH PROFINET
Originally conceived to operate over a wired network connection, PROFINET is a real-time industrial Ethernet protocol used for communication between industrial automation systems, such as programmable logic controllers (PLCs) and other devices in industrial environments. While it lives at layer seven of the ISO/OSI model and is typically transported over the data link layer using the 802.2 TCP/IP Ethernet standard.
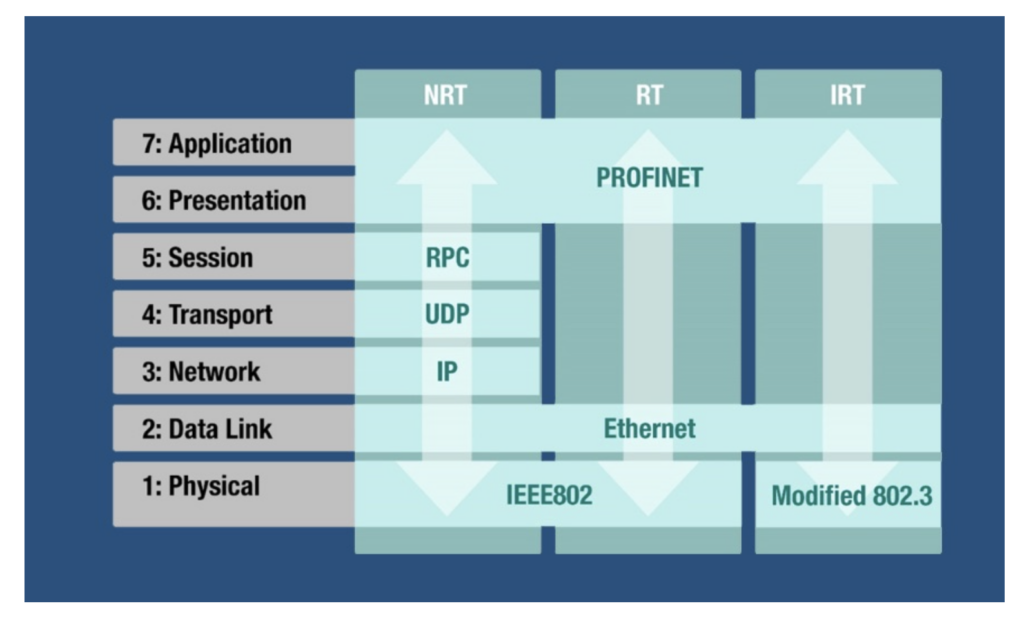
The protocol is found frequently in manufacturing oil and gas, chemical, and pharmaceuticals environments, such as assembly lines, robotic systems, and machine tools. It is used for process control, monitoring, and data acquisition– facilitating communication between different field devices, sensors, and control systems. This allows for seamless integration and coordination between different machines, robots, and control systems by enabling efficient coordination and synchronization of production processes.
PROFINET was developed for automation control communication to support time-critical tasks by reliably exchanging real-time data and precise control of processes between PLCs and various devices in an automation setting, relaying configuration capabilities, such as critical instructions telling automated robots where to go and what to do.
If these vital communications don’t reach systems in time, everything effectively stops.
A broadcast protocol operating at the data link layer (Layer 2), PROFINET was originally designed to work for devices wired to an Ethernet network. But as mobility takes hold within industrial environments, getting PROFINET to work over wireless has been an ongoing problem.
What’s more, ensuring the security of PROFINET communication over wireless is equally important, requiring robust encryption, device authentication, and deterministic access control mechanisms. While theoretically the PROFINET protocol can be transported over Wi-Fi, the practical reality is that the wireless medium just isn’t reliable enough to support the critical communications required to support essential OT systems using the protocol.
Unlike other industrial protocols, PROFINET requires deterministic and low-latency communication for many applications, especially those involving motion control or safety-critical systems.
Consequently, conventional best effort wireless network technologies, such as Wi-Fi, have never been well suited to support PROFINET due to variable latency, jitter and packet loss and retransmissions caused by factors such as interference, network congestion, and changing environmental conditions. These challenges effectively render expensive and important process production systems inoperable.
What’s more, industrial environments often have multiple wireless systems operating simultaneously, such as Wi-Fi, Bluetooth, and other proprietary wireless technologies. Ensuring that PROFINET can coexist with these systems without causing interference or performance degradation has also become a major challenge.
Fortunately, recent technical advances in private 5G LAN technology are solving these long-standing problems.
PRIVATE WIRELESS TO THE RESCUE
Private wireless networks operate in a relatively interference-free cellular spectrum (such as CBRS in the United States that uses the 3.55 to 3.7 GHZ frequency). Unlike conventional enterprise wireless alternatives such as Wi-Fi, Private wireless systems don’t rely on user equipment to make media access decisions. Like any cellular network, client access and mobility are strictly determined and centrally scheduled by the network that has a complete view into and control over the entire wireless infrastructure.
This is important as more and more systems become mobile and must hand off connections between different access points as they roam around. However, private 5G networks are, by definition, a routed infrastructure, operating at Layer 3 of the OSI stack. This has made supporting a link layer broadcast protocol, such as PROFINET problematic. Recent innovations in 5G LANs technology are making this a thing of the past.
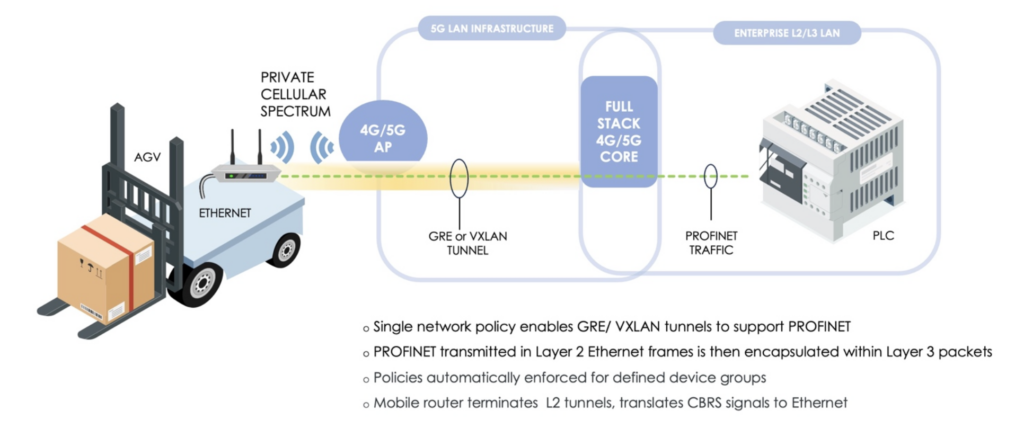
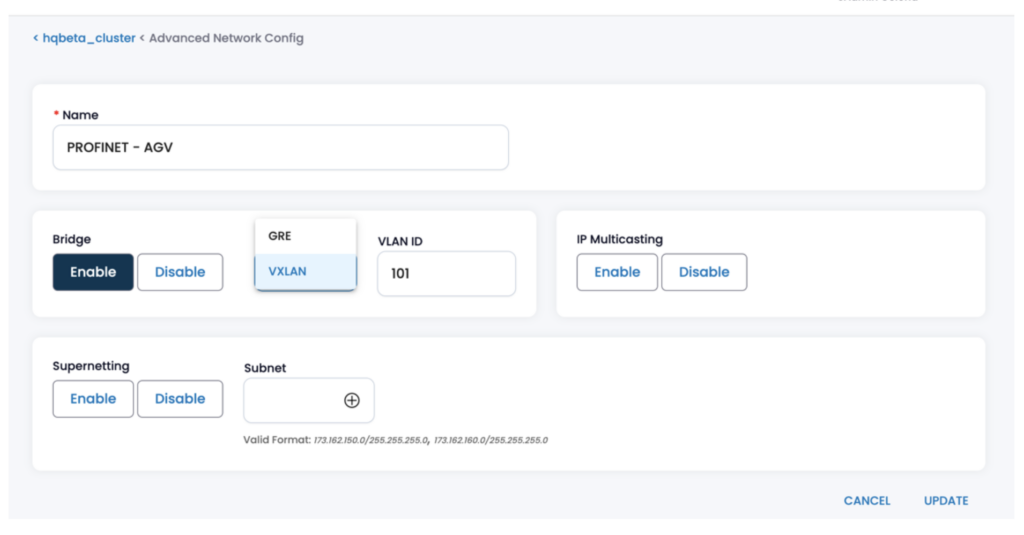
Using Layer 2 GRE (general routing encapsulation) or VXLAN (virtual extensible LAN) tunneling techniques, 5G LANs can now automatically establish tunnels from the core network to the customer premise equipment (CPE) connecting the end systems. PROFINET traffic transmitted in Layer 2 Ethernet frames is encapsulated within Layer 3 packets, which allows them to traverse network boundaries.
Because many of these process automation systems don’t support native cellular connectivity, mobile routers are used to reliably connect devices to the private wireless infrastructure, translating cellular signals, such as CBRS, to Ethernet packets. It is typically here where the VXLAN or GRE tunnels are terminated.
Within a centralized 5G LAN orchestration system, IT or OT administrators can easily enable this functionality by simply defining a device group and designating a single policy that automatically enforces strict latency, jitter, packet loss and throughput thresholds be automatically applied to traffic for that device group.
Since Layer 2 communication now takes place over the 5G LAN, a central controller can communicate with decentralized I/O modules on mobile devices such AGVs via PROFINET in a private 5G network and no local controls are needed on the individual AGVs.
This saves costs, reduces maintenance, and radically streamlines the operational burden for IT/OT staff who would otherwise be forced to manually configure individual tunnels for each system. New policy-based frameworks can make supporting protocols like PROFINET a zero-touch experience for IT and OT staff as admins can configure a single policy and have it automatically applied to hundreds of sites and thousands of devices.
From a security perspective, private wireless networks also offer enhanced security features essential to ensuring protected communications between PLCs and the end systems they are controlling. This includes L1-L7 data encryption, secure SIM-based device authentication, traffic segmentation and advanced access controls that provide industrial systems a higher level of security compared to conventional wireless alternatives.
Ultimately, as the industrial sector looks to super charge their automation efforts, new 5G LAN private wireless technology is ideally suited to overcome the reliability issues that have long inhibited successful implementation of PROFINET over wireless – delivering the deterministic connectivity, predictable quality of service and hardened security long needed by both IT and OT staff.
About the author
With extensive experience in software engineering, Aasawaree holds a master’s degree in computer science from Syracuse University. She specializes in wireless and telecommunications technology with domain expertise in product and system solutions engineering at companies including ThoughtWorks, Emptor, and Celona.

