Don’t let the little birthday cakes fool you — Verizon’s witty DBIR delivers serious warnings about growing cybersecurity threats
Verizon’s 2025 Data Breach Investigations Report (DBIR) reads different. It’s witty, oddly charming, and — yes — includes kiwi birds, robots and birthday cakes in its data visualizations. There are even occasional pep talks (“You rock!” it exclaims). But make no mistake: Behind the humor lies a stark warning. According to the report, there’s been an “alarming surge” in third-party cybersecurity incidents and attacks — a growing threat that’s reshaping the risk landscape for organizations of all sizes.
Now in its 18th edition, the DBIR analyzes more than 22,000 cybersecurity incidents, including 12,195 confirmed data breaches spanning 139 countries. Its scope is massive — and so is the message: Cyber threats are evolving fast, and businesses are struggling to keep up. Here are the key takeaways:
1. Third-party breaches double

Investigations Report
One of the most concerning findings is the doubling of third-party-related breaches, now making up 30% of all cases. Supply chains, software vendors and cloud platforms are increasingly becoming the weakest link in organizational defenses. Incidents like the MOVEit vulnerability and the Snowflake credential attacks exemplify how bad actors exploit trust-based relationships, often targeting misconfigured systems and a lack of multifactor authentication (MFA).
2. Vulnerability exploitation on the rise
Attacks that begin with the exploitation of unpatched vulnerabilities rose 34% year-over-year, now appearing in 20% of breaches. These include zero-day flaws in edge devices and VPNs — targets often left exposed due to the complexity of patching across distributed networks.
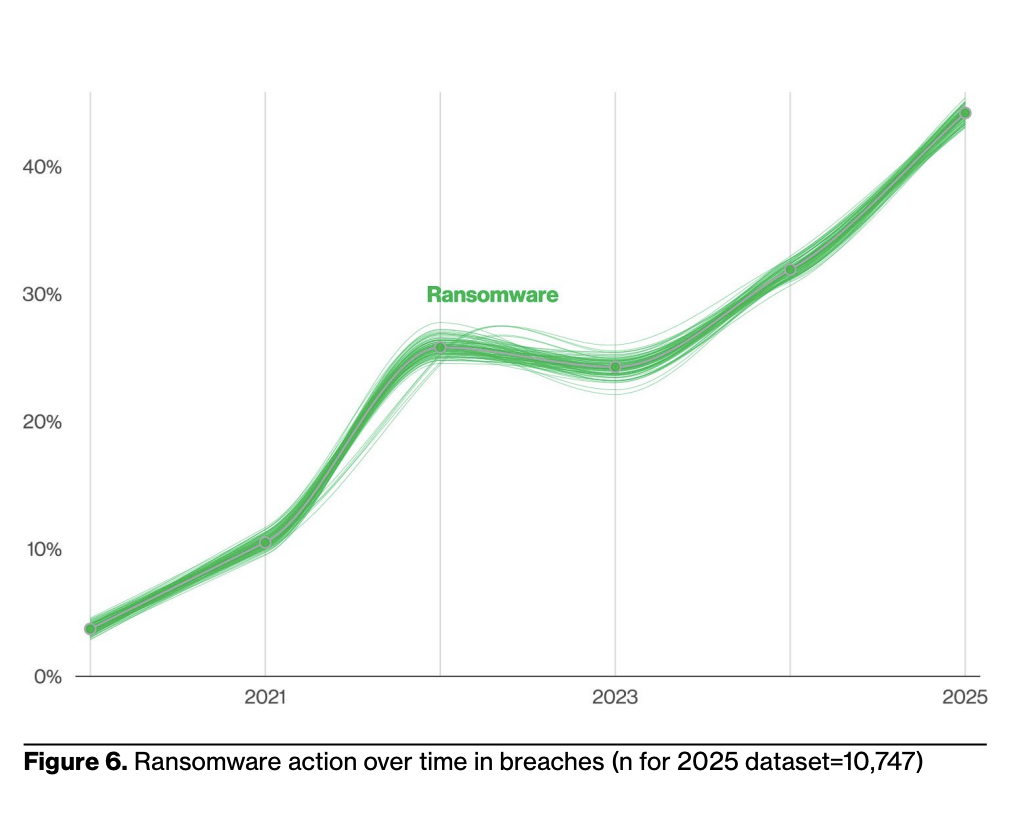
3. Ransomware’s tightening grip
Ransomware featured in 44% of breaches, a 37% increase from last year. While the median ransom payment declined to $115,000, its prevalence among small and medium-sized businesses (SMBs) is staggering — 88% of SMB breaches involved ransomware.
Still, some progress is evident. A growing number of victims are refusing to pay: 64% of affected organizations declined ransom demands, compared to 50% two years ago. This shift suggests greater awareness and improved preparedness across parts of the ecosystem.
As Craig Robinson, research VP at IDC, put it: “This year’s DBIR findings reflect a mixed bag of results. Glass-half-full types can celebrate the rise in the number of victim organizations that did not pay ransoms… Glass-half-empty personas will see… SMB-sized organizations are paying the price for their size.”
He added that while no silver bullet exists, Verizon’s continued work on raising “global awareness and cybersecurity readiness” remains vital.
4. Human error still central
The so-called “human element” remains ever-present. Approximately 60% of breaches involved social engineering, misdelivery or other forms of human error. Phishing remains a go-to tactic for attackers, while the median time to remediate leaked credentials on public repositories stands at 94 days — an eternity in breach terms.
5. Espionage and sector-specific threats
The report also highlights a notable increase in espionage-motivated breaches, now accounting for 17% of cases. Many of these involve state-sponsored actors, particularly in the manufacturing and healthcare sectors. Intriguingly, 28% of incidents linked to nation-state actors were financially motivated, blurring the line between classic espionage and opportunistic profit-seeking.
Other industries under continued threat include financial services, education and retail — with attackers shifting focus from payment card data to credentials and intellectual property.
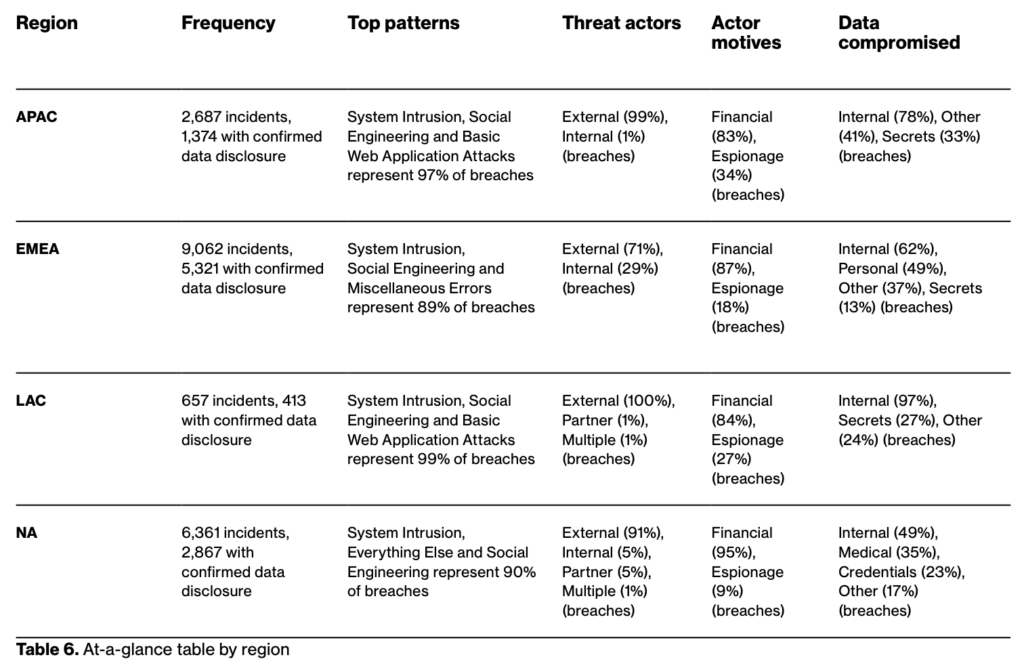
6. APAC and EMEA face intensifying attacks
In Asia-Pacific (APAC), system intrusions rose to 80% of breaches, with malware present in 83% and ransomware in 51%. In Europe, the Middle East and Africa (EMEA), system intrusions doubled and insider threats made up 29% of breaches — emphasizing the need for better internal controls.
7. The rising role of generative AI
Although generative AI (gen AI) is not yet dominant in attacks, its fingerprints are beginning to show. From AI-generated phishing emails to internal policy lapses where employees use gen AI tools on work devices without safeguards, the risk is real. The report urges organizations to draft and enforce clear usage policies for gen AI, especially in BYOD environments.
Cybersecurity recommendations
The DBIR recommends a multi-layered approach to defense that includes enforcing MFA and strong password practices; swiftly patching perimeter systems; conducting regular employee security training; the rigorous assessment and monitoring of third-party vendors; and establishing clear gen AI usage policies.
While playful in tone, the 2025 DBIR’s message is serious: Cybersecurity threats are escalating in complexity and impact. Organizations that don’t evolve their defenses in tandem risk becoming the next cautionary tale.