Argyle Data parcels out insight from a recent report to study the impact new and emerging mobile fraud types on operator revenues
The overall reported cost of fraud was reported as down from $46 billion in 2013 to $38 billion in 2015, according to the Communications Fraud Control Association’s study published late last year.
I don’t think anyone in the mobile operator community was expecting this. Indeed, operator responses to the survey indicated a widely held understanding that fraud had increased, as had fraud-related losses.
Before anyone starts celebrating, therefore, we need to take a more in-depth look at how the categories match up between 2013 and 2015, and what the details of the survey actually reveal. To understand more about what the figures are really saying, I analyzed both the 2015 and the 2013 CFCA reports. The results were surprising, revealing new classes of threats, and highlighting areas where the fraud management industry needs to do better for its mobile operator customers.
What we don’t know
One thing that struck me was when the survey asked, “over the past 12 months, do you think global fraud losses have trended up, trended down, or stayed the same?” 55.6% of respondents believed they had risen. Furthermore, 50% of respondents believed over the past 12 months, fraud within their own organization had trended up.
Overall, 88.9% of respondents – all from mobile operator companies – thought fraud had either gone up or stayed the same globally and 73.7% thought fraud had either gone up or stayed the same within their company. However, the numbers reported to the CFCA say fraud has gone down from $46 billion to $38 billion, which doesn’t make sense to me at all. Cybercrime is at an all-time high and an all-time level of sophistication. We obviously aren’t detecting everything that’s out there.
Donald Rumsfeld’s famous comment about “known knowns, known unknowns and unknown unknowns” could just as well refer to mobile revenue fraud. In the telco world this translates as known fraud attack techniques, fraud we suspect but can’t codify with rules, and fraud that we don’t know about and therefore can’t possibly look for.
The logical conclusion I came to was we are getting better at detecting known fraud attack techniques – that is why the numbers have gone down. The other part of this logic is that sophisticated criminals are getting much better at slipping past operator defenses with new attacks. The visible fraud bucket is reducing whereas the invisible bucket is increasing.
Sophisticated criminals using new techniques have a ready made cloak of invisibility when it comes to slipping past rules-based fraud detection systems. Communications providers are losing billions because of this. So my first question is, are we winning the wrong battle on fraud?
The world is moving to the use of big data and machine learning, and the users aren’t just good guys. They include organized crime – and even governments with a financial stake in misrouting traffic – deploying sophisticated attack patterns. The only way to win the battle will be for mobile operators to fight back in an equally sophisticated way.
The new mantra for defending subscribers and networks will be to use machine learning against vast data lakes to discover the “known unknowns” and “unknown unknowns.” And for this, fast, agile new technologies are required.
The new face of roaming fraud
In the 2013 study, roaming fraud was defined as “all types of fraud and abuse involving roaming.” But when you look at how roaming fraud is perpetrated, there are actually three common scenarios – home subscriber on a home network, (e.g. a U.K. subscriber on a U.K. network); roaming subscriber on a home network (e.g. a French subscriber on a U.K. network); home subscriber on a roaming network (a U.K. subscriber on a French network).
One of the things that always bothered me about the 2013 survey categories was that premium rate service fraud or international revenue share fraud, which are two major fraud types, can occur either on a home network or when roaming abroad. In 2013, roaming fraud was classed as just another fraud type sitting next to PRSF and IRSF. The 2015 survey has fixed this. Fraud types are now analyzed separately in roaming or in-network buckets. In 2015, IRSF is analyzed at a global level in 2015 as a combination of roaming ($7.1 billion) and in-network revenue share fraud ($3.7 billion). The combined total for IRSF is a staggering $10.8 billion.
There has been a dramatic change in the top 10 between 2013 and 2015. I’m drawing on our experience working with global mobile operators to try to explain this shift.
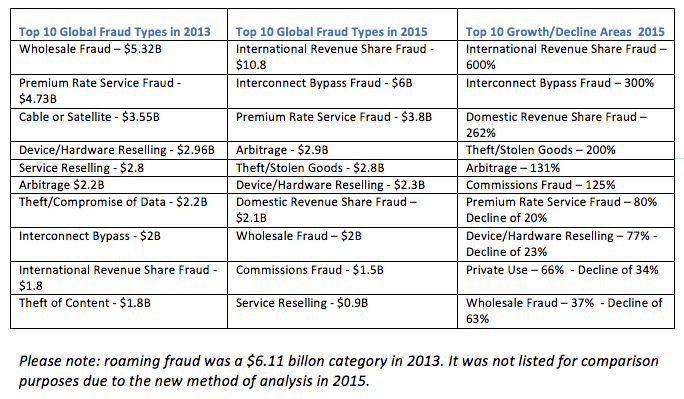
When you look at these numbers, one thing that sticks out is the growth of IRSF and the decline of PRSF, which was more than 2.6-times larger than IRSF in 2013. Now, IRSF is 28% of the fraud market alone. It is interesting to look at the definitions of these two types of fraud:
• International revenue share fraud – artificial inflation of traffic terminating to international revenue share providers (arbitrage).
• Premium rate service fraud – artificial inflation of traffic terminating to premium service providers.
There’s a reason for this. We are aware that some of the leading mobile operators have been moving to real-time fraud detection architecture and are therefore able to detect PRSF and bar the number more quickly. However, barring a number is much easier than barring a country. (The top 10 countries where fraud terminates are Cuba, Somalia, Bosnia and Herzegovina, Estonia, Latvia, Guinea, Serbia, Sierra Leone, United Kingdom and Lithuania.)
We also believe that as sophisticated arbitrage attacks are difficult to discover, the reported growth rate of 131% is far, far higher in reality. The rewards of mobile fraud are huge – minutes mean millions in some high volume attacks – so there is no reason to think that communications fraud attempts will ever slow down.
The purpose of this analysis is not to point fingers at the CFCA, but to illustrate the complexity and ever-changing nature of mobile revenue crime, and the need to match this sophisticated, innovative approaches with similarly inventive detection techniques.
Operators are aware that their efforts now need to focus on transforming unknown fraud types into something detectable and preventable. In a number of instances they are marshalling their defenses around real-time machine learning detection techniques. These allow almost instantaneous pinpointing of anomalies, such as hundreds of SIM cards registered to a single address, or a “roaming” user who has never made a call in the country from which they are supposed to be roaming.
Although the new frontiers of mobile fraud are constantly shifting, even the most creative mobile fraudsters leave digital fingerprints. The trick for the industry is to focus on the technologies that can throw an instant light on the traces criminals think are hidden. This is happening now.

Argyle Data CMO Ian Howells, Ph.D., is a passionate technologist and serial entrepreneur with over 25 years experience building successful technology companies through IPO and acquisition. Prior to joining Argyle Data, Howells has held senior marketing roles at Documentum from its early days through to IPO; SeeBeyond through its IPO and acquisition by Sun; Alfresco from a startup to the largest private open source company in the world; StorSimple, acquired by Microsoft; and Couchbase through a period of 400% growth. Howells has a Ph.D. in distributed databases and has published a number of papers and contributed to books on related topics. Howells has a passion for applying big data analytics techniques to marketing and open source. He previously penned the blog “Open Source Hearts and Minds” for Computerworld.
Editor’s Note: In an attempt to broaden our interaction with our readers we have created this Reader Forum for those with something meaningful to say to the wireless industry. We want to keep this as open as possible, but we maintain some editorial control to keep it free of commercials or attacks. Please send along submissions for this section to our editors at: dmeyer@rcrwireless.com.

