FBI vs. Apple case and the role mobile device management is playing
The issue of privacy and the law – particularly with respect to terrorism and the FBI – is challenging. A number of people have asked me where I sit regarding the current high profile case between the FBI and Apple over the iPhone that was recovered from Syed Rizwan Farook after his terrorist attack against employees of San Bernardino County where he worked.
While I do believe in privacy and individuals keeping their own information confidential, I also believe in the rule of law and, in particular, special provisions in any democracy to deal with mobile devices obtained by law enforcement from terrorists or others that break the law. Thus, I believe in protecting the information in devices owned by individuals, but point out that information on enterprise-owned smartphones is owned by the enterprise.
In the case of Farook’s iPhone, it was owned by San Bernardino County. The County was in the process of implementing mobile device management from MobileIron designed to enable the county to access all of the information on the phone. It’s too bad the full MDM software wasn’t yet installed on Farook’s iPhone. If it had been, then the county could have accessed the information and provided it to the FBI.
The county had begun the process. It had already implemented the MobileIron email component that enables county employees to access their county email using their iPhone. The next step was to add full MDM software so the device could be remotely managed, wiped clean if necessary or accessed as required by any law enforcement or government agency with proper court order.
Clearly, the FBI should be also be dealing with San Bernardino County. It would seem to me that since the county owned the device they could join with the FBI to request the bypass to the automatic trigger that would wipe the device clean after 10 unsuccessful password entry attempts. This issue must be resolved by the courts.
The MDM software from MobileIron is similar to what other MDM providers offer such as AirWatch by VMware, Citrix Systems and IBM. Thus, in cases where the device in question is owned and issued by an enterprise (vs. owned by the individual and not operating with the user’s enterprise network), it will be much easier to resolve requests by law enforcement and government agencies.
Going forward, we need to have some way to deal with the issues of mobile devices used by people for illegal activities. I leave it to the courts and law enforcement (including FBI) to address the issue.
I have put the different kinds of mobile device ownerships and access methods together below.
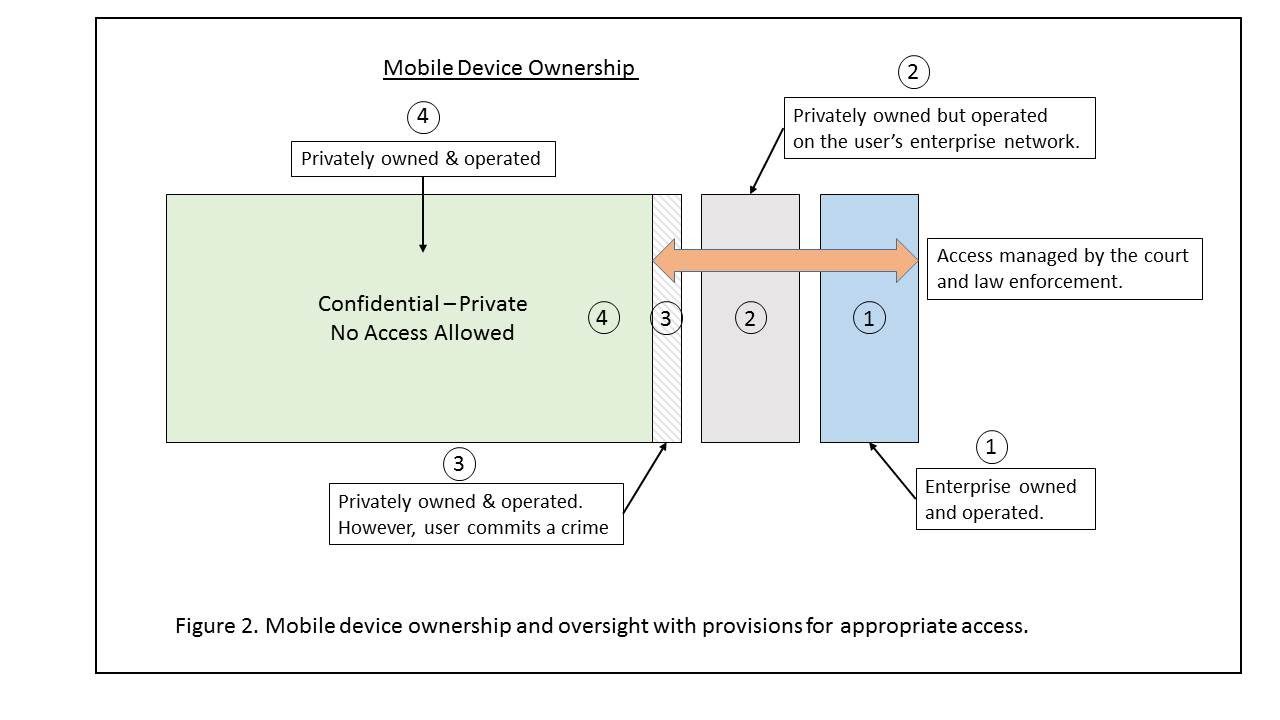
There are four different scenarios:
1. Enterprise owned and operated – In this scenario, the mobile device is owned and operated by the enterprise. The organization has MDM software installed that enables the enterprise to see the information that’s on the device at any time. If the enterprise doesn’t have MDM software, then they hopefully will have the information stored in a backup.
2. User owned, but enterprise operated – The user owns the device, but it operates on the enterprise network. At that point, the user has agreed that all of the enterprise information on the device is owned by the organization. The information that is owned by the user (e.g. their photos and music) can remain private and confidential by the owner. This is typically enabled through the use of digital locker in which the enterprise information is placed and held separate from the user’s personal data.
3. User owned, but crime committed – The user owns the device but then they commit a major (felonious or terrorist) crime. The courts and law enforcement decide what to do. If a “back door” is ruled to be required, then perhaps operating system vendors like Apple (iOS) and Google (Android) will be required to enable that kind of access.
4. User owned with no crime committed – In this scenario, the user owns the device and they have not committed a crime. In this scenario, the information is kept confidential.
Now, when there is a court order with adequate law enforcement (including the FBI) justification, each of the four situations is handled as follows:
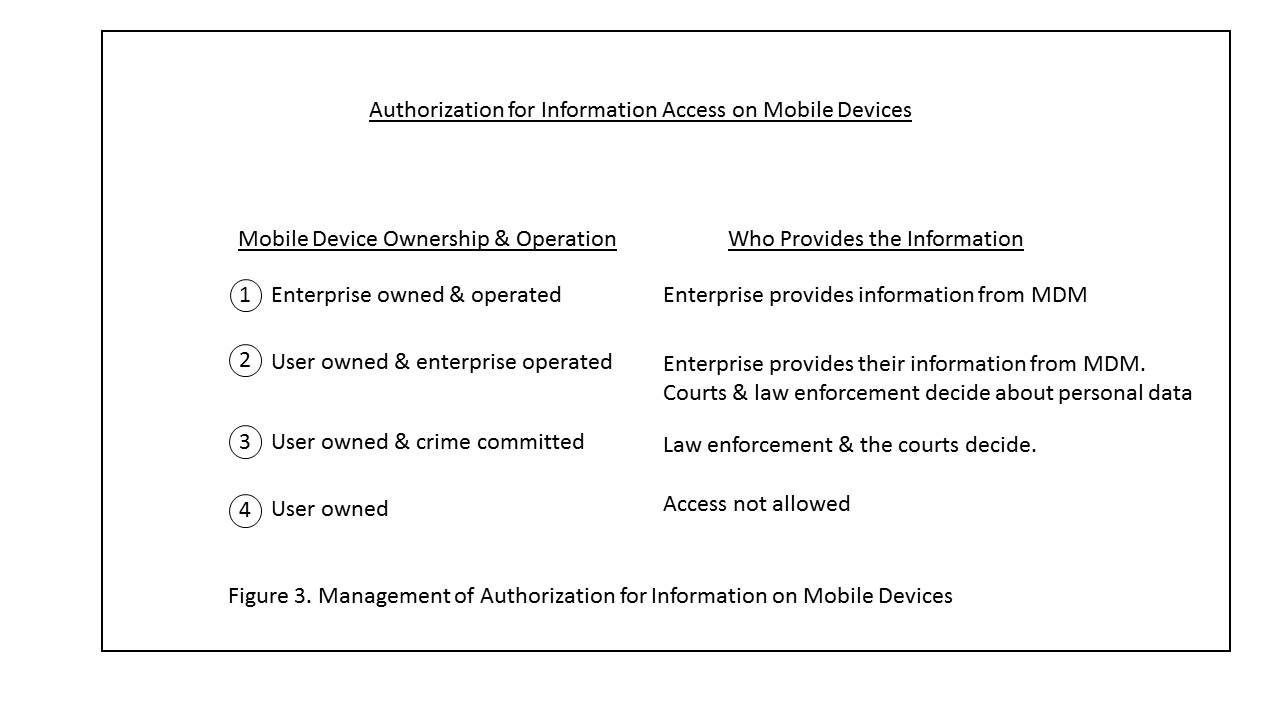
1. Enterprise owned and operated – The enterprise uses their MDM software to download the user’s data and provides it to the law enforcement organization, including the FBI. This was the ownership and operation class the terrorist was operating under in San Bernardino County. However, the county had not yet installed the components of the MobileIron MDM software to manage the contents of the device.
2. User owned, but enterprise operated – Once the user agrees to have their smartphone or tablet run on the enterprise network, then the enterprise has rights to the enterprise information. The enterprise either uses their MDM software to access and provide the information to the law enforcement organization, or if MDM software isn’t installed then they would have to provide the information from a backup that most organizations conduct. If the law enforcement organization needs access to the personal information, then they get the court order to do that. (I’ll let the courts, vendors like Apple and law enforcement organizations like the FBI work on resolution of how or when to provide access to a user’s information).
3. User owned, but crime committed – Hopefully on this scenario the user’s data is protected, but since we operate under the rule of law, if a (felonious or terrorist) crime has been committed and there’s a court order, then the courts and law enforcement will have to determine if the information must be accessed. The OS vendor then needs to work out a way to enable that to happen.
4. User owned with no crime committed – When the user owns the device and no crime has been committed then there should be no way in which anyone other than the user can access the information in the user’s mobile device.
I leave it to Congress, the courts and law enforcement agencies to determine to what extent personally owned, but locked smartphones should be able to be unlocked by anyone other than the owner.
J. Gerry Purdy, Ph.D. is the principal analyst with Mobilocity LLC and a research affiliate with Frost & Sullivan. He is a nationally recognized industry authority who focuses on monitoring and analyzing emerging trends, technologies, and market behavior in mobile computing and wireless data communications devices, software and services. Dr. Purdy is an “edge of network” analyst looking at devices, applications and services as well as wireless connectivity to those devices. Dr. Purdy provides critical insights regarding mobile and wireless devices, wireless data communications, and connection to the infrastructure that powers the data in the wireless handheld. Dr. Purdy continues to be affiliated with the venture capital industry as well. He spent five years as a venture advisor for Diamondhead Ventures in Menlo Park where he identified, attracted and recommended investments in emerging companies in the mobile and wireless industry. He has had a prior affiliation with East Peak Advisors and, subsequently, following their acquisition, with FBR Capital Markets. Dr. Purdy advises young companies who are preparing to raise venture capital. Dr. Purdy has been a member of the Program Advisory Board of the Consumer Electronics Association that produces CES, one of the largest trade shows in the world. He is a frequent moderator at CTIA conferences and GSM Mobile World Congress. Prior to funding Mobilocity, Dr. Purdy was chief mobility analyst with Compass Intelligence. Prior to that, he owned MobileTrax, LLC and enjoyed successful stints at Frost & Sullivan, Dataquest (a division of Gartner) among other companies.
Editor’s Note: Welcome to Analyst Angle. We’ve collected a group of the industry’s leading analysts to give their outlook on the hot topics in the wireless industry.

