Verizon’s annual examination of data breaches around the world found that most of the 100,000 security incidents over the past 10 years fall into one

of nine patterns — and that governmental or corporate espionage is increasingly driving attacks, with financial-based attacks on the decrease.
This is the seventh year that Verizon has published the examination of suspected and actual data breaches, and each year the company has been able to add more data sources, according to Marc Spitler, senior analyst and co-author of the Data Breach Investigations Report (DBIR).
“This report looks a lot different than its predecessors,” said Spitler, adding that having 50 contributors to the underlying data for the report substantially broadened its perspective.
The report analyzes more than 1,300 confirmed data breaches and more than 63,000 reported security incidents. Over the 10 years of data that Verizon is now including, there are about 100,000 incidents and more than 3,800 confirmed data breaches.
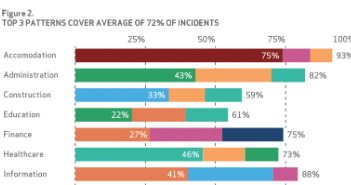
Verizon researchers looked back over data from the past decade this year, and were able to conclude that 92% of the security incidents fell into nine basic attack patterns, which vary from industry to industry.
“We thought that was very interesting, and very valuable,” Spitler said. “We want this to be actionable.”
Mobile has not been a significant contributor to overall network intrusions, Spitler said. He added that mobile security risks typically come in the form of attempting to get a foothold to internal networks via malware, or by stealing credentials from mobile devices to be used in penetrating wired connections.
The graph at right shows the distribution of types of attacks over various verticals. The nine patterns that Verizon identified include:
- miscellaneous errors such as sending an email to the wrong person
- crimeware (malware designed to gain control of systems)
- insider misuse or privilege misuse
- physical loss or theft
- Web app attacks
- denial of service attacks
- cyber-espionage
- point of sale intrusions
- payment card skimmers